Digital transformation which pivots on cloud applications and mobility is redefining the security perimeter and the interaction with services and digital assets by-pass the traditional perimeter-based security models. The network perimeter based security models doesn’t provide adequate security assurance with modern workflows.
The new perimeter is defined by every system that hosts, store or access services and data. The new perimeter model adapts to the complexity of modern computing environments and are founded on support for mobility, digital identities, devices, applications and data, wherever it may reside. These foundational elements form the core of the new security model and form the core concepts of Zero Trust Architecture (ZTA).
Zero Trust Architecture: New Era of Security
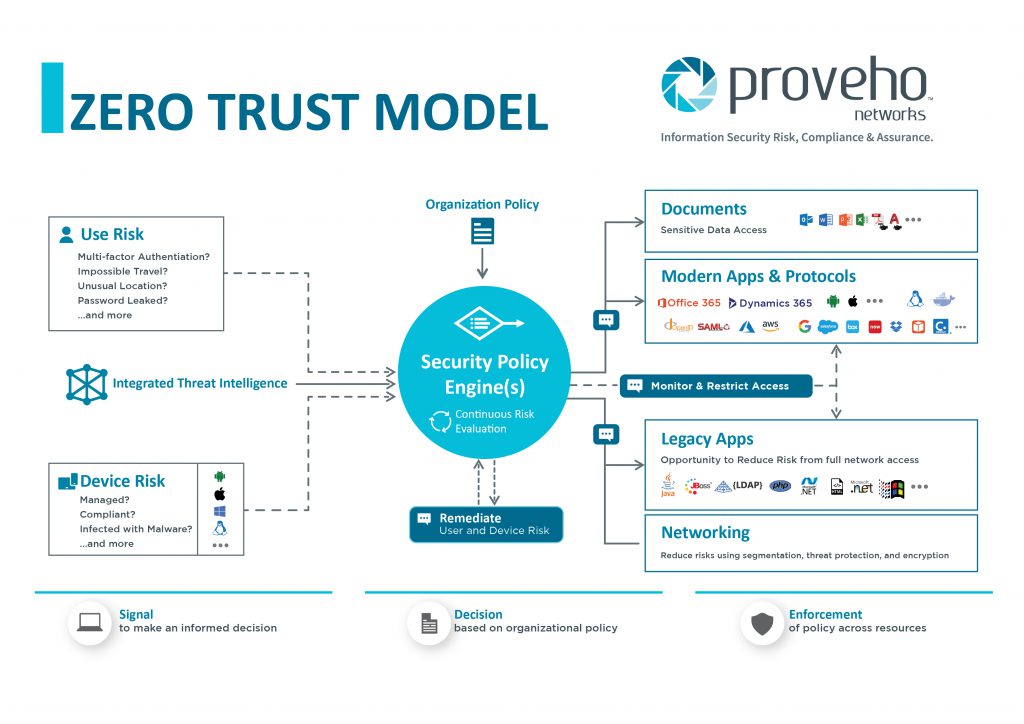
Zero Trust approach to security assumes that access all access is from untrusted network, this approach doesn’t trust the integrity of the network, device or identity where the request is originating from.
Zero Trust shifts the focus from network security to access controls that is based on dynamic user identity, device risk and other contextual signals. This enables information decisions on gated access to individual digital resources using established trust.
Digital transformation calls for a dual permitter approach to security. The network perimeter orientated security to protect legacy applications and networks and an identity driven strategy to securely adopt maturing cloud technologies and enable mobility.
Tier 1 technology vendors such as Microsoft recognise the need for security assurance across hybrid and fragmented computing domains and provided security capability that is available as a service and support for consumption-based billing.
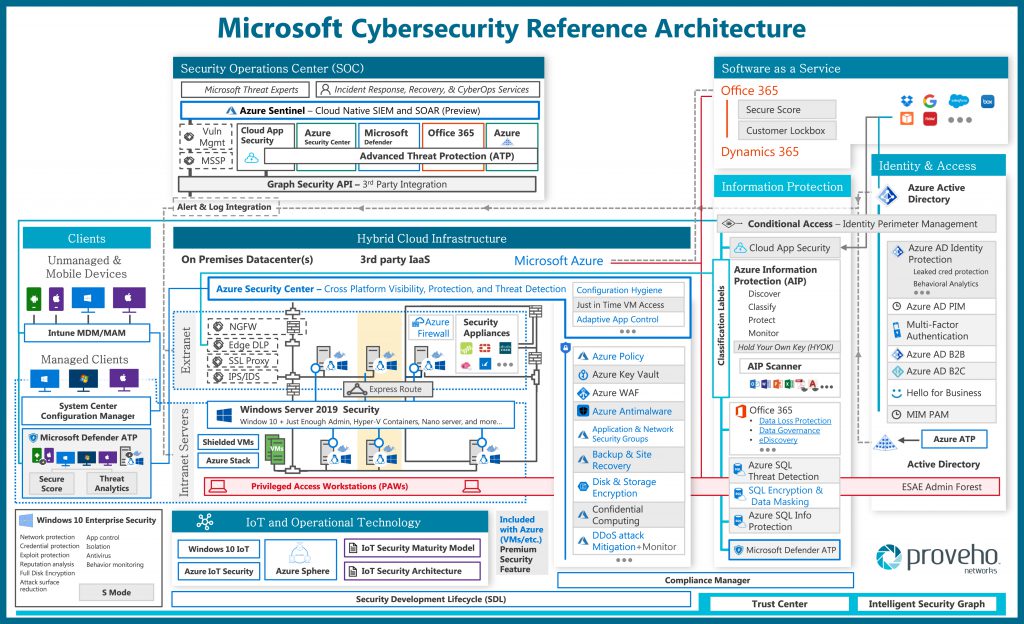
Digital transformation and security requirements changing the landscape dramatically, attackers ability to bypass conventional access controls highlights the deficiencies with traditional
security strategy and tools. Root cause of the issue is attributed to attacks that readily exploit the assumption that assets which are often mobile are safe on the trusted network. Zero Trust Model provides the architectural constructs and security capability requirements to ensure security assurance with modern computing.



